How to Process potential defects from static analysis tool using public JIRA system
PUBLISHED
Introduction
Static analysis can detect potential defects which can cause critical errors with just scanning or building the source code. The SVACE which is developed through years of joint development between Samsung Electronics and Ivannikov Institute for System Programming of the Russian Academy of Sciences (ISP RAS http://www.ispras.ru) has been adapted to Tizen platform development to prevent critical errors at the Code Review phase.
1 Static Analysis Tool (SVACE) Overview
A. Static (code) Analysis
i. The analysis of computer software that is conducted without executing the program
ii. Just scanning or building with analysis tool can detect potential defects which can cause critical faults
B. SVACE Tool
i. The potential defects can be prevented using SVACE tool at the Code Review Stage
ii. All developers have to review the potential defect
1. True Alarm : modify the relevant code and make new patch set
2. False Alarm : upload the JIRA ignore request post
2 Potential defect detection for Tizen Platform
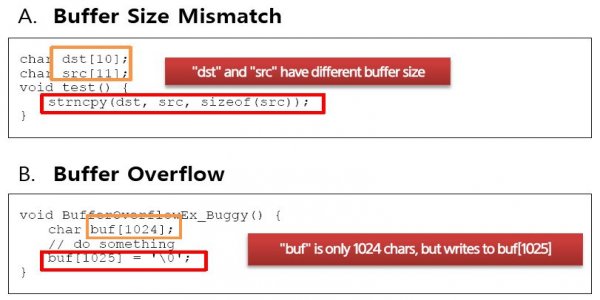
Buffer Size Mismatch Issues • finds situations where a size parameter passed to "safe" versions of standard functions (such as strncpy or memset) is unsafe (out of local buffer bounds).
Buffer Overflow Issues Finds situations : • where a dynamic array (that is, buffer) is accessed by a constant index, whose value is outside of the size of buffer. • when a variable is used as an index of a buffer but the variable may have value outside of the boundary of the buffer. • when the value of an index used to access a buffer is checked with a bound that is less strict than necessary. • where a fixed-size array is accessed at a constant index outside its range.
Use After Free / Release Issues • finds situations where a memory location is accessed through a pointer that has just been deallocated. • finds situations where a pointer referencing deallocated memory is deallocated again.
Memory / Resource Leak Issues • Detects where memory was allocated, and then all references to that memory are lost, before release has been performed • Detects where a resource such as a file descriptor, a file handle, or a socket descriptor, is lost since a local resource variable that held its value went out of scope or was re-assigned
NULL Dereference Issues • finds situations where first, a pointer is compared to NULL (which indicates that it could have a NULL value), and then it is dereferenced (unconditionally) • situations where a pointer is dereferenced, but can only have NULL value, and so the operation of dereference can never be run without causing a runtime error
Security Issues • reports warnings for the use of unsafe library functions including gets() and strcpy() • detects case whan scanf is used without size check. Reading string from a I/O stream can be a vulnerable point
3 Source Code Checking Example
4 Jira Ignore Request Process
1) Connect to https://bugs.tizen.org/projects/TINF
2) Login with Tizen account
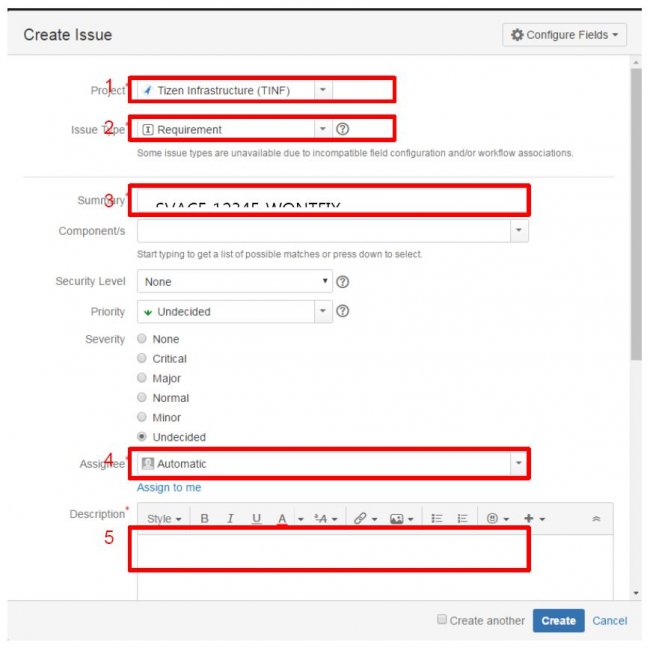
3) Click ‘Create’menu like below.
4) Fill the request form using below guideline.
- Project : Tizen Infrastructure(TINF)
- Issue Type : Requirement
- Summary : SVACE [WGID Number] [WONTFIX / FALSEPOSITIVE]
# WONTFIX : This warning might be a defect, but it will not make any trouble in this code
# FALSEPOSITIVE : This warning does not making any trouble
- Assignee : SA_Auto(sa.swc@samsung.com)
- Description : Please write the reason why this warning should be ignored
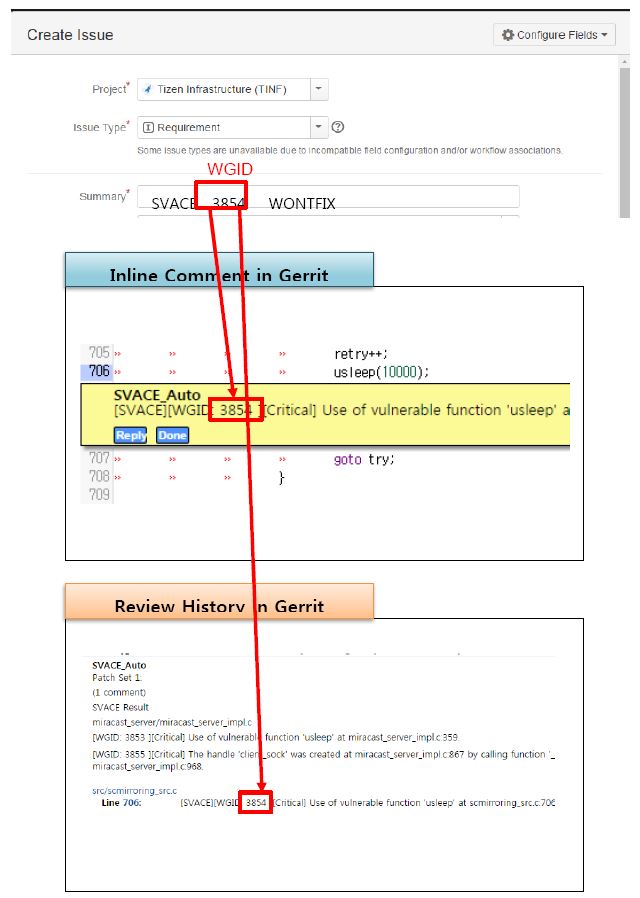
- You can find the WGID from “Inline Comment”or “Review History”as below
5) SA_Auto will process your Ignore Request within 10 minutes.
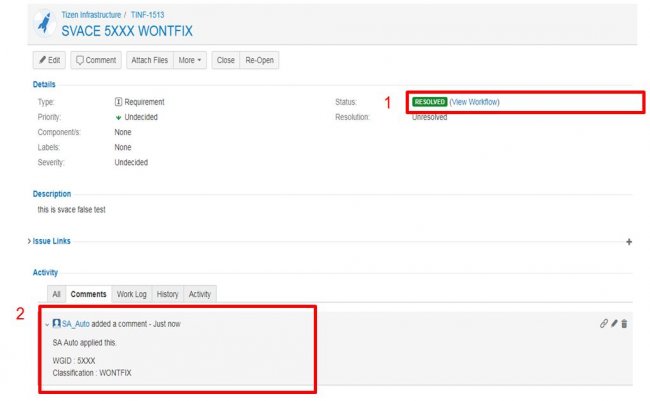
- After your Ignore Request is processed, the status of JIRA will be changed to “RESOLVED” and SA_Auto writes the comment within 10 minutes.
- After this, SVACE won’t report the same warning again
1. Status : RESOLVED
2. Comments : Add a comment regarding warning